Purpose of Hash Function
Purpose of a hash function is to verify the integrity of a message. Message authentication is a mechanism or service used to achieve authentication. Message authentication and hash function assure that data received are exactly as sent by sender. (i.e., contain no modification, insertion, deletion, or replay). In many cases, there is a requirement that the authentication mechanism assures that provide identity of the sender is valid. When a hash function is used to provide message authentication, the hash function value is often referred to as a message digest.
Application of hash function Using Symmetric Key Cryptography
#1 - In above figure, hash code is generating from message and then appended to message. The message plus concatenated hash code is encrypted using symmetric encryption. Because only A and B share the secret key(K), the message must have come from A and has not been altered. The hash code provides the structure or redundancy required to achieve authentication. Encryption is applied to the entire message plus hash code, confidentiality is also provided.
#2 - In above figure, hash code is generated from given message. After generation of hash code, it is encrypted using secret key (K). Then encrypted hash code is append with original message and send to the receiver. It reduces the processing burden for those applications that do not require confidentiality.
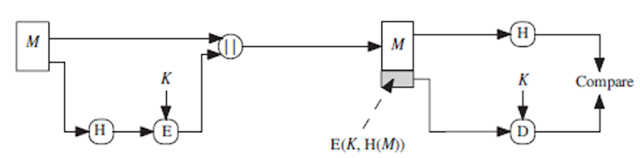
#3 - It is possible to use a hash function but no encryption for message authentication. The technique assumes that the two communicating parties share a common secret value S. A compute the hash value over the concatenation of M and S, appends the resulting hash value to M. Because B possesses, it can recompute the hash value to verify. Because the secret value itself is not sent, an opponent cannot modify an intercepted message and cannot generate a false message.
#4 - Confidentiality can be added to the approach of previous method by encrypting the entire message plus the hash code. When confidentiality is not required, method (2) has an advantage over methods (1) and (4), which encrypts the entire message, in that less computation is required.
Application of hash function Using Asymmetric Key Cryptography
#1 - Another important application, which is similar to the message authentication application, is the digital signature. Purpose of digital signature is verify sender’s signature to achieve authentication. In the case of the digital signature, the hash value of a message is encrypted with a user’s private key PRa. Anyone who knows the user’s public key PUa can verify the integrity of the message. It also provides a digital signature, because only the sender could have produced the encrypted hash code.
#2 - In above figure, hash code is encrypted using user’s private key. Then encrypted hash code appended to the message. Now, message plus hash is encrypted using symmetric secret key (K). Using above diagram, we can achieve confidentiality as well as authentication. Figure A and B both are hash code based digital signature.
Realtime application of Hash Function
Hash functions are commonly used to create a one-way password file. A hash of a password is stored by an operating system rather than the password itself. Thus, the actual password is not retrievable by a hacker. Who gains access to the password file?
In simple terms, when a user enters a password, the hash of that
password is compared to the stored hash value for verification. This approach
to password protection is used by most operating systems. Hash functions also
can be used for intrusion detection and virus detection.
To learn more about Application of Hash Function, Click here







No comments:
Post a Comment